Exposed to Cyber Threats?
CyberSecurity
SMEs Protection
Protect your network from unwanted traffic and improve your online security with our monitoring solution that not only detects but also block malicious traffic. The specific integration, developed with Python code, makes it easy to identify, block individual or range-based traffic, and make exceptions. With our success stories and individualized data management approach, you can be assured that your online security incidents will be properly identified and expertly managed.
Easy, experience effortless protection as we automate the neutralization of cyber threats. Furthermore, weekly and monthly reporting plus reporting ad-hoc meticulously crafted tailored to meet your network’s specific requirements.
Components
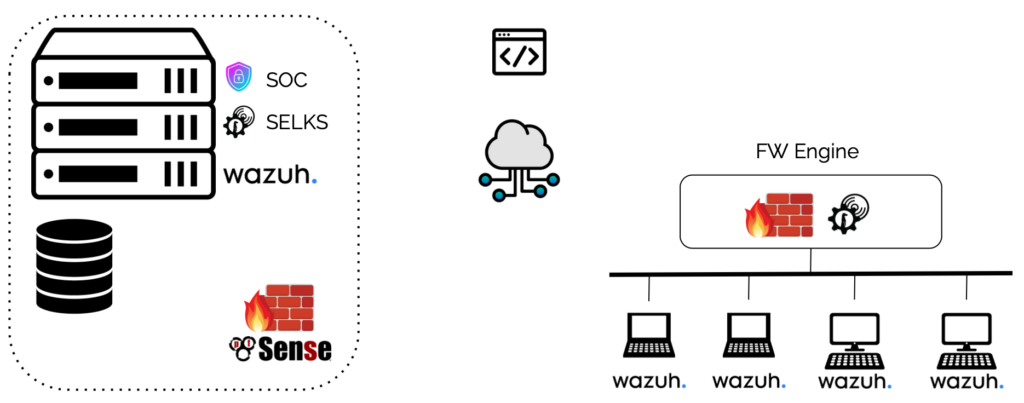
SELKS & Wazuh are two open-source cybersecurity platforms that focus on detecting and preventing cyber attacks, however they are different in architecture and functionality:
SELKS is a network security solution which includes a comprehensive set of tools such as Suricata (intrusion detection system IDS / intrusion prevention system IPS), network security monitoring (NSM) and threat hunting capabilities.
Wazuh is a unified extended detection and response (XDR) system and security information and event management (SIEM) system that can detect cyber threats on multiple operating systems, including Windows, Linux, and macOS. It works by installing agents on client systems that send data to a central server for event analysis and correlation.
The main difference between SELKS and Wazuh is the way they are structured and how they collect and analyze security data. SELKS is a complete solution that runs on a virtual machine or dedicated hardware, while Wazuh relies on agents installed on client systems that send data to a centralized server.
Integration
SELKS and Wazuh can work together to enhance security. SELKS is an IDS/IPS system based on Suricata, and Wazuh is a security platform that combines vulnerability detection, log monitoring, threat detection, and compliance management.
When used together, SELKS and Wazuh can provide comprehensive security for systems and networks. SELKS can detect and prevent malicious activities on the network, while Wazuh can monitor and respond to other security threats such as system or application vulnerabilities, abnormal logs, and compliance issues. By using both solutions, system administrators can have a more complete view of the security of their systems and networks and can respond to a wider range of security threats.
System Architecture

The perfect match with Zero Trust
What is Zero Trust?
Previously, cybersecurity strategies have traditionally relied on the concept of a network perimeter to safeguard valuable data and essential assets.
These strategies would involve familiar tools such as Firewalls and VPNs, which are utilized to examine and authenticate network traffic entering and exiting the private network.
Nevertheless, the process of digital transformation and the shift towards remote work are compelling companies to reconsider their operational approaches. It has become evident that the existing security strategy centered around the network perimeter is no longer adequate.
At the present, internal users are accessing an increasing number of cloud services from various locations. Given this scenario, it has become crucial for users and devices to securely and efficiently access critical data.
Consequently, the Zero Trust model was developed to meet the needs of this new data-driven cloud environment. It aims to provide adaptive and continuous verification, ensuring the protection of users, devices, data, and assets. In essence, zero-trust network access seeks to encompass security around every user, device, and connection for any given transaction.
Are you interested in learning more? Keep reading for a brief overview of the Zero Trust strategy:
Zero Trust security model
The Zero Trust Network model was defined in 2010 by John Kindervag, a researcher at Forrester.
As a result, the Zero Trust model is increasingly being implemented across enterprises as the pressure to protect data and systems intensifies during the COVID-19 pandemic.
The key aspect to understand about Zero Trust is that it is not a standalone product or tool. Instead, it is a framework centered around enforcing strict access controls and not trusting anyone by default.
Least-privileged access is a core principle of Zero Trust, assuming no inherent trust for users or applications. It prioritizes minimal access privileges based on specific needs and roles.
Zero Trust operates on the assumption that everything is potentially hostile, and trust is established based on factors like user identity, context, security posture, and requested application.
The Zero Trust Model leverages existing technologies and governance processes to achieve its objective of securing the enterprise environment. Here are a few examples you might be familiar with:
• Multi-Factor Authentication
• Identity and Access Management (IAM)
• Secure Web Gateway (SWG)
• Orchestration
How the Zero Trust security model works
The Zero Trust Architecture is an extensive security approach that offers a comprehensive safeguarding of vital assets within an organization.
Although Zero Trust security strategies can differ depending on an organization’s network environment, there are certain key elements that any Zero Trust network should encompass:
• Log and inspect all network traffic
• Limit, control and verify user access & identity
• Verify, access and secure all network resources
Securing the Modern Workplace through Zero Trust
At its essence, Zero Trust assumes hostility and blocks untrusted communication unless specific attributes are identified for workloads.
As a result, this approach provides robust security that remains intact as workloads communicate, regardless of the environment. It ensures protection across various network environments, securing applications and services effectively.
Getting started with Zero Trust
Numerous organizations have already implemented components of Zero Trust, including tools like Multi-Factor Authentication and Identity and Access Management (IAM). These elements contribute to the implementation of micro-segmentation in specific parts of the environment.
Nevertheless, Zero Trust is not solely focused on deploying specific technologies; it revolves around the fundamental concept that access is granted only after individuals have demonstrated trustworthiness.
Consider the following factors when implementing a Zero Trust framework:
• Terminate every connection: Zero Trust should terminate each connection, allowing for inspection of files before they reach the endpoint, rather than relying on a “passthrough” approach
• Protect data with granular policies based on context: Zero Trust should utilize user identity, device posture, and specific business policies to verify users. These policies should be adaptive, adapting to changing contexts and user requirements
• Eliminate the attack surface: Zero Trust should establish one-to-one connections, reducing the risk of lateral movement within the network. This helps prevent compromised devices from infecting other network resources
Comprehensive Zero Trust implementation
Regrettably, the implementation of Zero Trust is a unique journey for each organization and can present complexities for some.
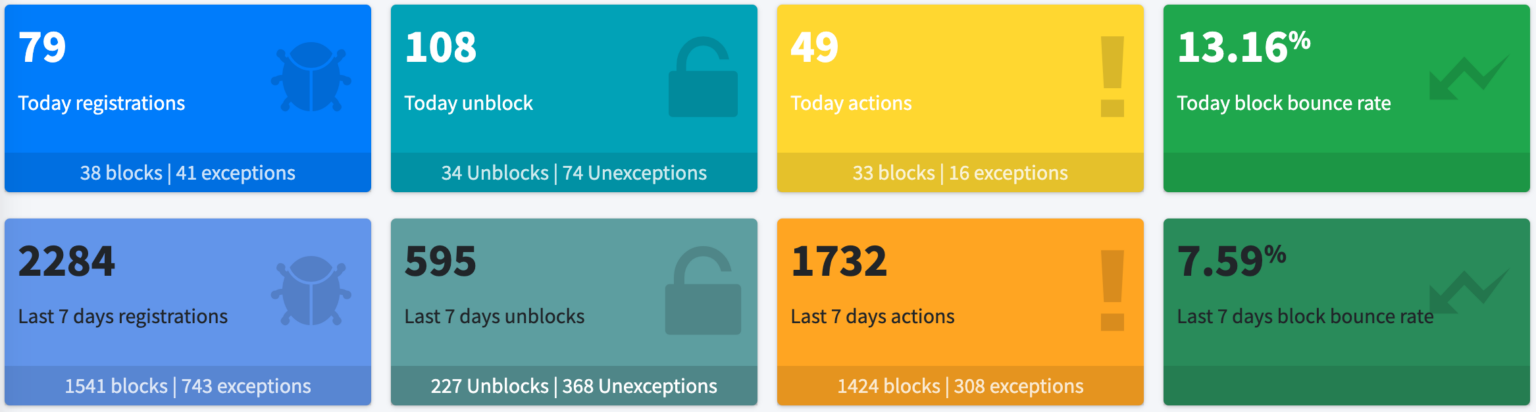
Get your real-time Dashboard and monitor your critical security events